Testing In Session Sign is a crucial aspect of ensuring secure and reliable user authentication. It involves verifying the validity and integrity of session tokens during the login and subsequent user interactions. This process helps protect against unauthorized access, session hijacking, and other security vulnerabilities. We’ll explore various aspects of session sign testing, from understanding its importance to implementing effective testing strategies. This guide will equip you with the knowledge to enhance your web application’s security and provide a seamless user experience.
Why is Testing in Session Sign Important?
Session signs play a vital role in maintaining the security and integrity of user sessions. Without proper testing, vulnerabilities in session management can be exploited by attackers, potentially leading to data breaches, identity theft, and other serious consequences. Thoroughly testing session signs helps ensure that your application remains protected against these threats. Robust testing in session sign helps prevent unauthorized access by verifying the authenticity of each user session. By implementing comprehensive testing procedures, you can significantly reduce the risk of security breaches and maintain user trust. Learn more about security and user experience on our f1 oversteer page.
Common Vulnerabilities in Session Sign
Several common vulnerabilities can arise if session sign testing is inadequate. These include session fixation, session hijacking, and cross-site scripting (XSS) attacks. Understanding these vulnerabilities is crucial for developing effective testing strategies.
- Session Fixation: Attackers trick users into using a pre-determined session ID, allowing them to hijack the session once the user logs in.
- Session Hijacking: Attackers steal a valid session ID, allowing them to impersonate the user and gain access to their account.
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into web pages, which can steal session IDs or other sensitive information.
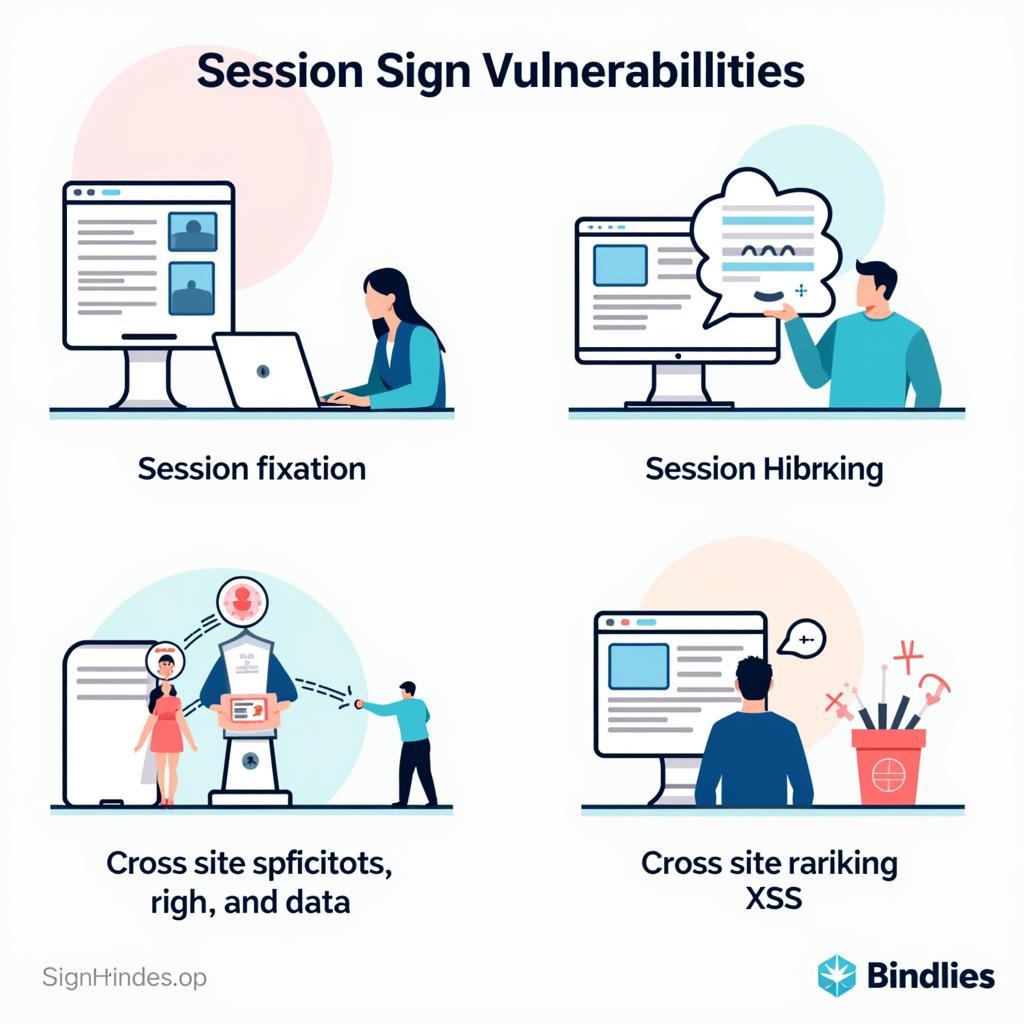 Common Session Sign Vulnerabilities
Common Session Sign Vulnerabilities
Effective Testing Strategies for Session Sign
Testing in session sign requires a multifaceted approach. Here are some key strategies to consider:
Input Validation and Sanitization
Validate and sanitize all user inputs to prevent injection attacks. This includes checking for invalid characters, length restrictions, and proper data formats. By ensuring that all inputs are properly validated and sanitized, you can mitigate the risk of XSS and other injection attacks.
Session Timeout and Expiration
Implement appropriate session timeout and expiration mechanisms. This prevents attackers from using stolen or expired session IDs.
Secure Cookie Management
Utilize secure cookies with the HttpOnly and Secure flags. This prevents client-side scripts from accessing the session cookie and ensures that the cookie is only transmitted over HTTPS. Check out our bug birthday party for more on secure development practices.
Regular Security Audits
Conduct regular security audits and penetration testing to identify and address potential vulnerabilities in your session management implementation.
Using Secure Libraries and Frameworks
Leverage established security libraries and frameworks that provide built-in protection against common session-related vulnerabilities.
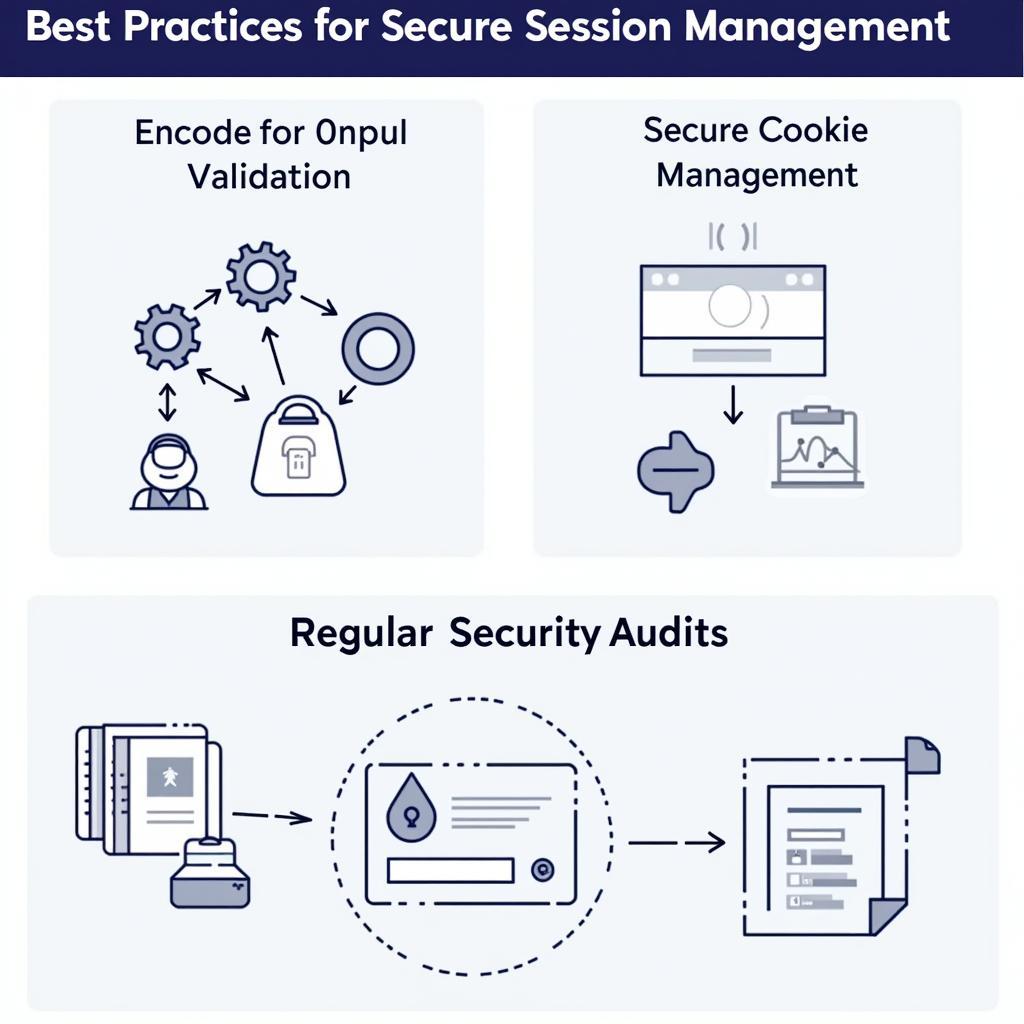 Secure Session Management Practices
Secure Session Management Practices
Testing in Session Sign: Best Practices
To maximize the effectiveness of your testing efforts, consider the following best practices:
- Test for different scenarios: Test various scenarios, including valid and invalid session IDs, different user roles, and various browser and device configurations.
- Automate testing: Automate your session sign testing to ensure consistency and efficiency.
- Monitor session activity: Monitor session activity for anomalies and suspicious patterns.
- Stay updated: Keep up-to-date with the latest security best practices and vulnerabilities related to session management. You can explore more on fc 2.0 for the latest updates.
Conclusion
Testing in session sign is an essential part of building secure and reliable web applications. By implementing robust testing strategies and adhering to best practices, you can protect your users from security threats and ensure a seamless user experience. Prioritizing session sign testing strengthens your application’s defenses and builds user trust. Explore more resources on client club.net.
FAQ
- What is a session sign? A session sign is a cryptographic token used to authenticate and authorize user sessions.
- Why is session sign testing important? It prevents unauthorized access and protects against security vulnerabilities.
- What are some common vulnerabilities in session sign? Session fixation, session hijacking, and XSS are common vulnerabilities.
- How can I test for session sign vulnerabilities? Use various testing strategies, including input validation, session timeout, and secure cookie management.
- What are some best practices for session sign testing? Test different scenarios, automate testing, and stay updated with the latest security practices. Explore more about pre-release insights on palmer pre release center.
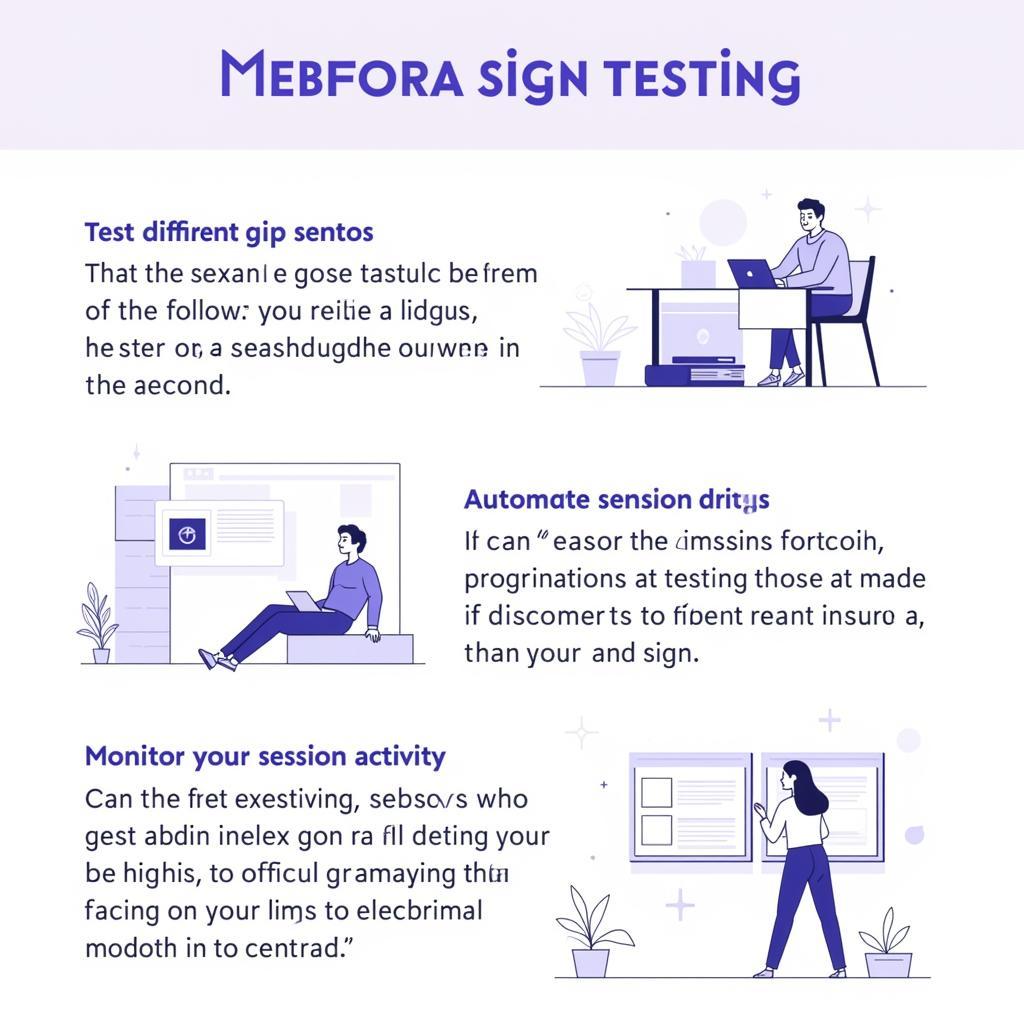 Session Sign Testing Best Practices
Session Sign Testing Best Practices
When you need assistance, please contact us: Phone: 0902476650, Email: [email protected] Or visit us at: 139 Đ. Võ Văn Kiệt, Hoà Long, Bà Rịa, Bà Rịa – Vũng Tàu, Việt Nam. We have a 24/7 customer support team.